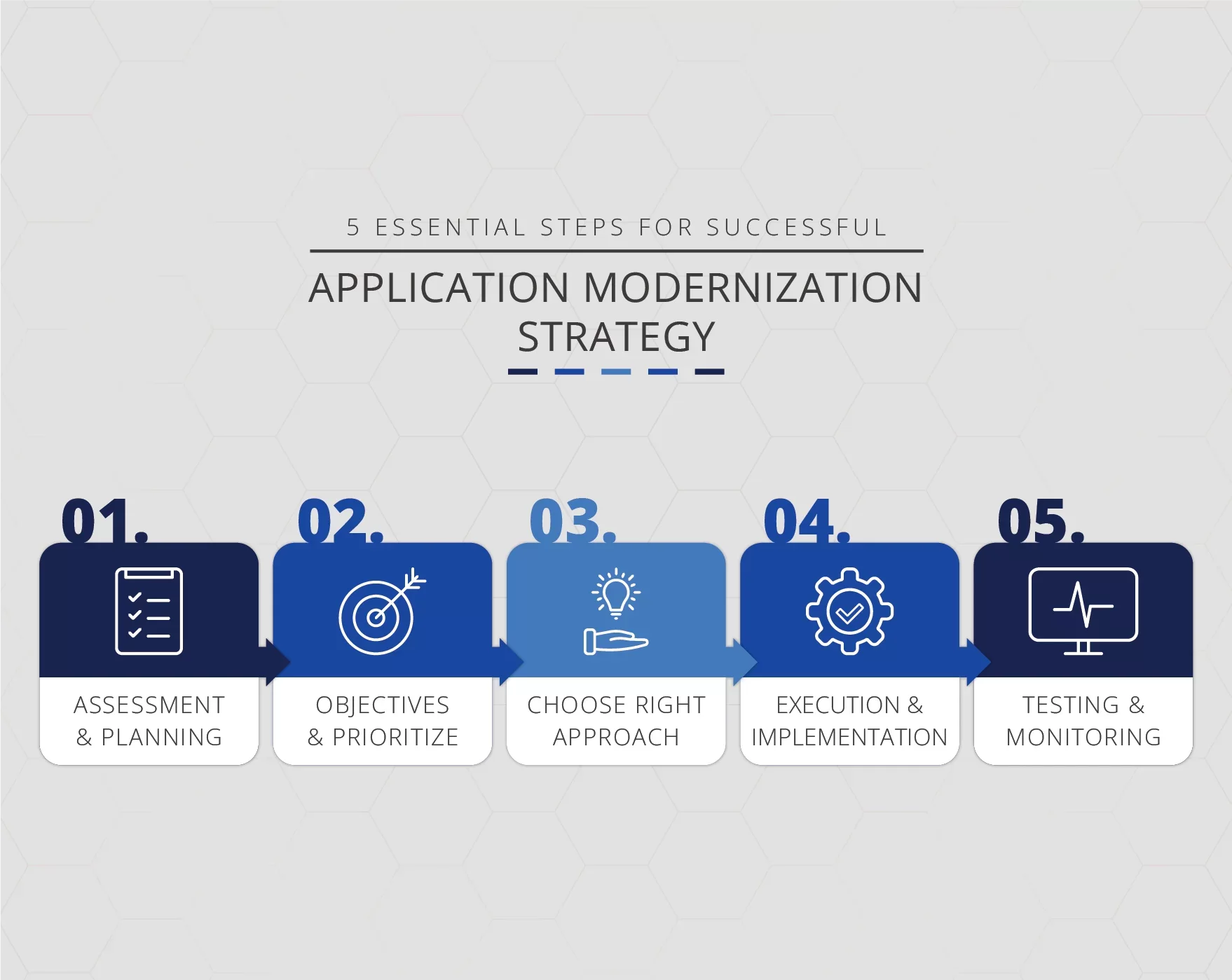
5 Essential Steps for Successful Application Modernization Strategy
In today's dynamic digital landscape, businesses must continuously evolve to remain competitive. Application modernization is a crucial strategy for organizations looking to enhance their operational efficiency, leverage new technologies, and meet the ever-changing demands of their customers. This process involves updating older software for newer computing approaches, including newer languages, frameworks, and infrastructure platforms.
For many companies, especially those relying on legacy systems, application modernization can be a daunting task. However, with the right strategy, it can lead to significant benefits such as improved performance, better security, and reduced operational costs. This blog delves into the basics of application modernization strategies, offering insights into how organizations can effectively navigate this complex but rewarding journey. Whether you're an IT leader or a business executive, understanding these foundational elements is essential for driving successful digital transformation initiatives.
1. Assessment and Planning
A successful application modernization strategy begins with a thorough assessment and meticulous planning. This foundational step ensures that businesses have a clear understanding of their existing systems and infrastructure, paving the way for informed decision-making and effective modernization efforts.
Importance of Conducting a Comprehensive Assessment
Conducting a comprehensive assessment is crucial for identifying the strengths and weaknesses of current applications and infrastructure. This assessment provides valuable insights into the existing environment, highlighting areas that require improvement and modernization. It helps businesses understand the scope of the project, set realistic expectations, and align modernization goals with overall business objectives.
Key Factors to Consider During the Assessment Phase
- Business Goals: Define the overarching business goals that the modernization effort aims to achieve. This includes improving operational efficiency, enhancing customer experience, and driving business growth.
- User Needs: Understand the needs and expectations of end-users. Gather feedback and analyze user behavior to identify pain points and opportunities for improvement.
- Technical Debt: Evaluate the existing technical debt, which includes outdated technologies, legacy systems, and other technical liabilities that hinder performance and scalability.
Practical Tips and Resources for Assessment
- Conduct Surveys and Interviews: Engage with stakeholders, including employees, customers, and partners, to gather diverse perspectives on current systems and identify areas for improvement.
- Utilize Assessment Tools: Leverage specialized assessment tools and frameworks that can provide a detailed analysis of the existing infrastructure and applications.
- Seek Professional Guidance: Consider partnering with experienced IT consultants or service providers who can offer expert insights and recommendations based on industry best practices.
By following these steps, businesses can build a solid foundation for their modernization journey, ensuring they are well-prepared to navigate the complexities and challenges ahead.
2. Define Objectives and Prioritize Applications
Defining clear objectives and prioritizing applications are critical steps in an effective application modernization strategy. These steps ensure that modernization efforts are aligned with business goals and focused on areas that will deliver the greatest impact.
Defining Clear Objectives and Goals
To start, businesses need to establish clear objectives and goals for their modernization efforts. This involves identifying the desired outcomes and setting measurable targets. Key objectives might include:
- Enhancing Performance: Improving the speed and efficiency of applications to meet user expectations and reduce operational costs.
- Boosting Security: Upgrading systems to address security vulnerabilities and comply with industry regulations.
- Improving User Experience: Creating a more intuitive and engaging user interface to increase user satisfaction and retention.
Prioritizing Applications
Once objectives are defined, the next step is to prioritize applications for modernization. This can be done by evaluating each application based on several factors:
- Business Impact: Assess how critical each application is to the business’s core operations. High-impact applications that drive revenue or support essential functions should be prioritized.
- User Experience: Consider the user experience associated with each application. Applications that are frequently used by customers or employees and have a significant impact on user satisfaction should be high on the priority list.
- Technical Feasibility: Evaluate the technical complexity of modernizing each application. Applications with lower technical debt and higher feasibility should be considered first to achieve quick wins.
Real-World Examples and Case Studies
To illustrate successful prioritization strategies, consider these real-world examples:
- Construction Industry: Bechtel, a global construction and engineering company, focused on construction industry software development to modernize its project management system. By implementing advanced IT solutions, they improved project tracking and reduced delays, leading to higher client satisfaction and better resource management.
- E-commerce and Retail: H&M, a multinational clothing company, prioritized e-commerce software development to continuously upgrade its online platform. By integrating advanced IT solutions, they enhanced site performance and user experience, resulting in a significant boost in sales and customer retention.
- Education and ELearning: Coursera, an online learning platform, invested in education industry IT services to enhance their e-learning system. By modernizing their platform, they provided a more interactive and engaging learning experience, leading to increased student enrollment and satisfaction.
- Property Management: Greystar, a global leader in rental housing property management, focused on property management software development to streamline their operations. By integrating advanced IT solutions, they improved tenant management and communication, resulting in more efficient operations and higher tenant satisfaction.
By defining clear objectives and strategically prioritizing applications, businesses can ensure that their modernization efforts are both effective and aligned with their overall goals.
3. Choose the Right Modernization Approach
Selecting the appropriate modernization approach is crucial for the success of any application modernization strategy. Let's delve into the key considerations when making this decision.
Explore Different Approaches
Application modernization can take various forms, each with its own set of advantages and challenges. Businesses may consider options like re-platforming, re-hosting, refactoring, or rebuilding. Re-platforming involves migrating applications to a new platform without altering their core architecture, offering a quicker and less disruptive path to modernization. Re-hosting moves applications to the cloud or a new infrastructure environment with minimal changes. Refactoring involves restructuring existing code or architecture to improve performance, scalability, or other attributes, while rebuilding entails completely rewriting applications from scratch to leverage modern technologies and architectures.
Evaluate Business Requirements
It's essential to align the chosen modernization approach with the overarching business objectives. Consider factors such as desired outcomes, budget constraints, and time-to-market requirements. For example, if the primary goal is to reduce operational costs and increase scalability, re-platforming or re-hosting might be suitable options. However, if the objective is to enhance user experience and enable future innovation, refactoring or rebuilding could be more appropriate.
Assess Technical Feasibility
Assessing the technical feasibility of each modernization approach is critical to avoiding potential pitfalls. Factors such as the complexity of the existing application architecture, availability of skilled resources, and compatibility with future technology trends should be evaluated. A thorough analysis will help determine whether the chosen approach is feasible within the given constraints and aligns with the organization's long-term IT strategy.
Make Informed Decisions
The decision-making process should be guided by a comprehensive understanding of the pros and cons of each modernization approach. Seeking input from key stakeholders, including IT professionals, business leaders, and end users, can provide diverse perspectives and insights. By weighing the trade-offs and potential benefits of each option, businesses can make informed decisions that maximize the value of their modernization efforts while minimizing risks.
4. Execution and Implementation
Executing an application modernization plan requires careful planning, coordination, and execution. Let's explore some best practices to ensure a successful implementation.
Align Stakeholders and Resources
One of the first steps in executing a modernization plan is to ensure alignment among key stakeholders, including business leaders, IT teams, and end users. Clear communication of objectives, expectations, and timelines is essential to garner support and commitment from all parties involved. Additionally, adequate resources, including budget, personnel, and technology infrastructure, should be allocated to support the modernization effort effectively.
Minimize Disruptions and Mitigate Risks
Minimizing disruptions during the implementation phase is crucial to maintaining business continuity and user satisfaction. To achieve this, businesses should conduct thorough risk assessments and develop mitigation strategies to address potential challenges or setbacks proactively. Strategies may include conducting pilot tests, implementing phased rollouts, or establishing fallback mechanisms to revert to previous versions if necessary. Additionally, robust change management practices, such as training programs and user support services, can help ease the transition for stakeholders affected by the modernization process.
Leverage Monitoring and Tracking Tools
To track progress, monitor performance, and address issues in real time, businesses can leverage various monitoring and tracking tools. These tools provide valuable insights into the effectiveness of modernization efforts, allowing stakeholders to identify areas for improvement and make data-driven decisions. From application performance monitoring (APM) tools to cloud management platforms, there are numerous options available to suit different business needs and preferences. By leveraging these tools effectively, businesses can optimize the modernization process and ensure the successful implementation of their plans.
5. Testing, Monitoring, and Continuous Improvement
After the execution phase, the journey towards successful application modernization continues with thorough testing, vigilant monitoring, and a commitment to continuous improvement.
Thorough Testing for Reliability and Security
Testing is a critical aspect of the modernization process, ensuring that modernized applications meet the highest standards of reliability, security, and performance. Businesses should establish robust testing frameworks and protocols to systematically evaluate the functionality, usability, and security of modernized applications. This includes conducting various types of tests, such as unit testing, integration testing, and security testing, to identify and address any issues or vulnerabilities before deployment.
Implementing Automated Testing Processes
To streamline the testing process and enhance efficiency, businesses can leverage automated testing tools and frameworks. Automation helps accelerate testing cycles, reduce manual errors, and improve test coverage, allowing teams to detect and resolve issues more quickly. By incorporating automated testing processes into their workflows, businesses can increase agility, lower testing costs, and deliver high-quality modernized applications at scale.
Vigilant Monitoring for Performance Optimization
Once modernized applications are deployed, continuous monitoring is essential to ensure optimal performance and reliability. Monitoring tools enable businesses to track key performance metrics, identify performance bottlenecks, and proactively address any issues that may arise. By monitoring application performance in real time, businesses can optimize resource utilization, improve user experience, and mitigate the risk of downtime or service disruptions.
Embracing a Culture of Continuous Improvement
Finally, successful application modernization is not a one-time event but an ongoing journey of continuous improvement. Businesses should foster a culture of continuous improvement, where teams regularly gather feedback from users, analyze performance metrics, and prioritize enhancements based on evolving needs and market trends. By embracing agility, adaptability, and innovation, businesses can stay ahead of the curve and ensure that their modernized applications remain competitive and relevant in today's rapidly evolving digital landscape.
Conclusion
In conclusion, a successful application modernization strategy involves a thorough assessment and planning phase, a clear objective setting, choosing the right modernization approach, effective execution, and continuous testing and improvement. By following these essential steps, businesses can transform their legacy systems to meet modern demands, enhance performance, and provide a superior user experience. Engaging with IT consulting services can provide the necessary expertise and support to navigate this complex process, ensuring that modernization efforts are efficient and aligned with long-term business goals. Remember, modernization is not a one-time project but an ongoing journey toward continuous improvement and innovation.

Learn More
Ready to Build? Partner with Hexagon for IT Expertise and Commitment
Learn More
Let’s Chat About Your Next Project!
Our team is eager to get to know your business and assess if our services align with your objectives. Just complete the form and we'll reach out for an informal discussion about your business needs – no commitment required.
CALL OUR U.S LOCATION
EMAIL U.S SALES
Lets Connect
Stay in Touch
Let’s Chat About Your Next Project!
Privacy Policy | Terms & Conditions | ©2025 Hexagon IT Solutions










